Russia goes phishing
Intelligence agencies confirm Russia’s interference in the 2016 election
Credit: Georgia Panitz
February 10, 2017
Much controversy exists surrounding the certainty and the degree to which Russia interfered in the U.S. presidential election. President Trump has made controversial statements regarding the ability of U.S. intelligence agencies to determine who is responsible for the multiple hackings of organizations, such as the Democratic National Committee (DNC). By investigating technological clues, however, it is possible for agencies to determine who is responsible for a hack.
The Obama Administration released a report which said that Russia hacked the DNC and initiated other cyber activity in an attempt to harm Hillary Clinton’s electability, such as producing negative propaganda and paying Internet trolls. In their official report, the CIA, FBI and NSA stated that they have high confidence of this. The CIA and FBI also have “high confidence” that this cyber activity was done to elevate Trump’s election chances, while the NSA only had moderate confidence. The Department of Homeland Security is cited in the report as stating that Russia did not affect the actual vote tallying.
While it is very difficult to pinpoint a hacker from a single hack, the intelligence community as well as multiple cybersecurity firms have been able to deduce Russia’s involvement. This is possible since when hacks are completed, they leave a trace. Hackers tend to reuse some of the same code in their hacks. These are known as signatures, and by matching these signatures, it can be determined that a group that made one hack is also responsible for another.
The hackers involved in the DNC incident had previously hacked other entities tied to Russian interests, such as military and political targets in Ukraine and Georgia. The intelligence and cybersecurity communities believe Russia is the only plausible source that has interests in all these places.
This knowledge, along with the information that the hackers were usually active during working hours in the Moscow Timezone, led intelligence community members such as Matt Tait, the CEO of cybersecurity firm Capital Alpha Security, to believe beyond all reasonable doubt that Russia is responsible for the hack.
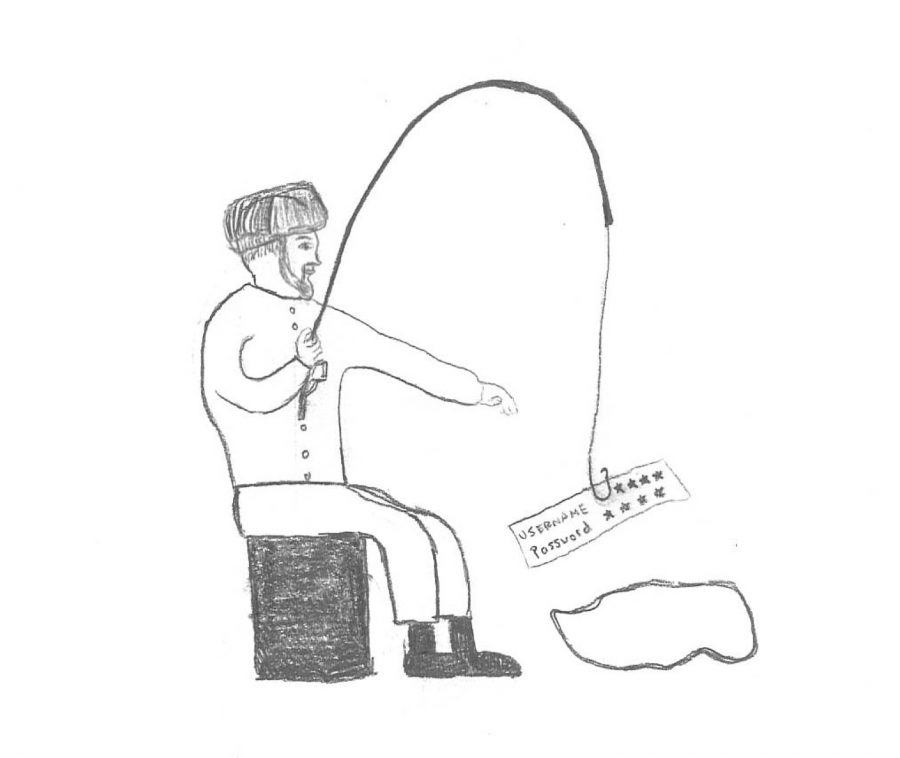
The hackers were able to enter the DNC server by using a simple but effective method known as phishing. Phishing often occurs when people see a link such as https://myaccount.google.com/security, and assume that the link goes to the URL shown. However, this link can be linked to something completely unrelated. Phishers often link it to a website they created that looks very similar to the link written down. Phishing websites often asks for credit card information, passwords, security questions, and even social security numbers. Victims often unknowingly give their information away, assuming it is going to the website falsely simulated by the hackers. As effective as phishing can be, it is easy to avoid. Before people enter any passwords or other personal information, researching the website can help prevent important information from being used by hackers. Through phishing, Russian hackers were able to obtain information from members of the DNC, including many documents, some of which the Russians shared with Wikileaks. The documents released by Wikileaks were also a major point of controversy this election cycle.